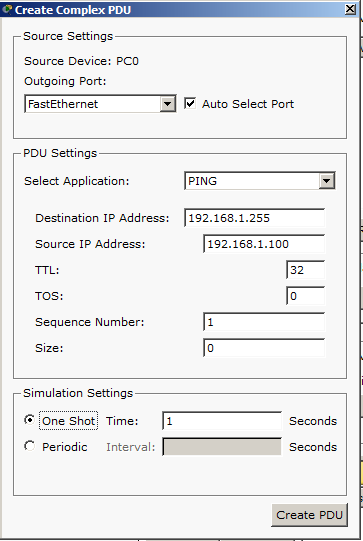
The latest amplifiers exist in all shapes and sizes. Finding the ideal model for your application can frequently be tricky. There is a large number of different names and terms describing audio amplifiers, just like "Class D" or "T-amp". Furthermore, every maker shows a large amount of specs, including "SNR", "dynamic distortion" and so on. I will describe the term "amplifier wattage" a bit more in this editorial. "Output power" is one of the most essential terms describing amplifier functioning. On the other hand, it is time and again misunderstood. Several makers also in history have used this term in a perplexing way to hide the real performance.
Several of the terms which amplifier suppliers make public often are confusing and do not inevitably offer a good indication of the real functioning of the amp. Now I am going to give several details in relation to "amplifier output power". This term is often misunderstood. It is essential to look rather closely at how the maker shows this rating.
Wattage is either shown as "Watts peak" which means the amplifier may create brief bursts of this amount of power or "Watts rms" which shows how much wattage the amplifier may deliver for a longer amount of time. In the past, manufacturers have customarily favored showing the "peak power". This number is bigger than the average or "rms" power. On the other hand, "peak power" can often be deceptive since there is no standard stating the period of time that the amplifier must be able to provide this level of output power.
Nowadays most amps will denote rms power that gives a better indication of the amp's real performance. Though, please make certain that your amp offers adequate headroom to steer clear of clipping of the audio. Having sufficient headroom is crucial since music signals differ a great deal from sine wave signals that are used to quantify rms output power. Brief peaks of large power are frequently found in audio signals. These bursts are going to drive the amp into large distortion unless the peak power is big enough.
Please notice that often the peak output power of the amp is going to depend on the impedance of your speakers which is commonly between 4 and 8 Ohms. Resulting from the limited amplifier supply voltage, the maximum output wattage will be half if you attach an 8-Ohm loudspeaker of the peak power that the amp is able to output to a 4-Ohm loudspeaker. Frequently highest power is specified for a 4-Ohm speaker impedance. On the other hand, ideally the maker will tell which speaker impedance the output power rating is being referenced to. Please note that several amplifiers cannot drive speakers with extremely low loudspeaker impedance.
Several of the terms which amplifier suppliers make public often are confusing and do not inevitably offer a good indication of the real functioning of the amp. Now I am going to give several details in relation to "amplifier output power". This term is often misunderstood. It is essential to look rather closely at how the maker shows this rating.
Wattage is either shown as "Watts peak" which means the amplifier may create brief bursts of this amount of power or "Watts rms" which shows how much wattage the amplifier may deliver for a longer amount of time. In the past, manufacturers have customarily favored showing the "peak power". This number is bigger than the average or "rms" power. On the other hand, "peak power" can often be deceptive since there is no standard stating the period of time that the amplifier must be able to provide this level of output power.
Nowadays most amps will denote rms power that gives a better indication of the amp's real performance. Though, please make certain that your amp offers adequate headroom to steer clear of clipping of the audio. Having sufficient headroom is crucial since music signals differ a great deal from sine wave signals that are used to quantify rms output power. Brief peaks of large power are frequently found in audio signals. These bursts are going to drive the amp into large distortion unless the peak power is big enough.
Please notice that often the peak output power of the amp is going to depend on the impedance of your speakers which is commonly between 4 and 8 Ohms. Resulting from the limited amplifier supply voltage, the maximum output wattage will be half if you attach an 8-Ohm loudspeaker of the peak power that the amp is able to output to a 4-Ohm loudspeaker. Frequently highest power is specified for a 4-Ohm speaker impedance. On the other hand, ideally the maker will tell which speaker impedance the output power rating is being referenced to. Please note that several amplifiers cannot drive speakers with extremely low loudspeaker impedance.
About the Author:
Check out this web site in order to read through further info concerning t class amplifiers.